Information Security
Information Security Efforts
The Kyocera Group recognizes the importance of information resources and aims to strengthen information security. To serve as a trusted member of society, Kyocera has established the Basic Information Security Policy, which defines Kyocera's information security objectives, measures, and action guidelines. Through promoting this policy, we continuously strive to prevent and reduce information security risks.
Basic Information Security Policy
With the expansion of cyberspace, the Kyocera Group continues to strive to understand the importance of all its information assets and to strengthen the handling of those assets. To respond to the trust of society as a whole, including our customers, business partners, investors, employees, and other stakeholders, we have established a basic information security policy, and declare that we will carry out our business in accordance with this policy.
Purpose
The purpose of the basic policy is to establish basic rules regarding information security measures to be implemented by the Kyocera Group in order to maintain the confidentiality, integrity, and availability of the information assets held by the Kyocera Group.
Scope of application
This basic policy applies to information assets (including personal information) related to all business activities managed by the Kyocera Group.
Information security management system
To protect and appropriately manage information assets, the Kyocera Group has established the Information Security Committee, and the Chief Information Security Officer is responsible for overall information security management.
Compliance with laws and contractual requirements
The Kyocera Group regularly investigates information security requirements, and strictly follows the various laws and regulations of each country, the guidelines and norms of each country, and industry standards and our contractual obligations with business partners.
Education and training for employees
The Kyocera Group understands our social responsibility with regard to appropriately handling information assets, and provides constant education and training that are necessary for employees to appropriately use and manage information assets.
Implementation of measures
The Kyocera Group will endeavor to prevent the occurrence of information security incidents by implementing information security measures against external attacks and threats of internal fraud. These measures will be appropriate to the type of information asset. In the event of a violation of laws or regulations, breach of contract, or an incident related to information security, we will immediately and appropriately resolve the situation and implement recurrence preventive measures.
Regular evaluation and continuous improvement
To respond to changes in the business environment and social conditions while maintaining information security, the Kyocera Group will regularly evaluate our information security management system and the implementation status, and continuously formulate and implement improvement plans.
July 1st, 2022
Goro Yamaguchi, Chairman of the Board and Representative Director
Hideo Tanimoto, President and Representative Director
Kyocera Corporation
ISO27001Certificate of Registration
Kyocera Corporation
Kyocera Group (Japan)
Governance System
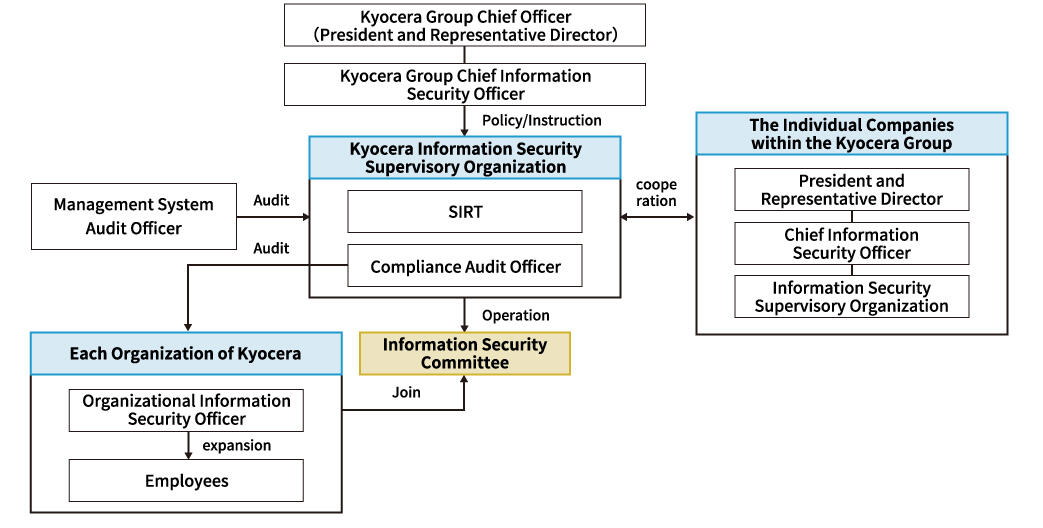
The Kyocera Group promotes effective measures through the establishment of an information security governance system headed by the President and Representative Director, and continues to work diligently to improve the level of information security throughout the Group. As the Kyocera Group's Chief Officer, the President and Representative Director, oversees the entire information security system. In addition, under the direction of the Kyocera Group Chief Information Security Officer, the organization in charge of information security plays a central role in promoting the planning and implementation of security measures, and ensures thorough education on these measures throughout the Group.
To strengthen information security measures across the entire Group, the information security management organization works closely with Kyocera Group companies. They have established a Security Incident Response Team (SIRT) to promptly respond to and analyze security incidents, and to formulate recurrence prevention measures.
In addition to this important function, the Information Security Committee comprises the organization in charge of information security and the organizational information security officer appointed by each organization with the task of examining measures while sharing and coordinating the progress of and identifying issues with the information security measures in each organization.
Matters decided by the committee are disseminated to all employees through the organizational information security officer of each organization to raise information security awareness throughout the Group.
Providing support for the effectiveness of these functions, the Compliance Audit Officer conducts audits of each organization, and the Management System Audit Officer conducts audits of the organization in charge of information security to continuously evaluate the efficacy of the information security system.
Going forward, we will continue to work together as a group to strengthen and maintain information security.
Implementation of Information Security Training
The Kyocera Group conducts information security training based on Kyocera Group Information Security Regulations. In order to raise awareness about information security and inform employees of their responsibilities, specialized training relating to the maintenance and management of information security is provided, in addition to annual training for new employees, general training for all employees, and training for managers.

Procedures and Countermeasures in the Event of an Emergency
According to the Kyocera Group Information Security Regulations, an “incident” is defined as "a situation that threatens business operations or information security as a result of an undesired or unexpected occurrence or accident related to information security." These regulations also state the measures to be taken in the event of an incident and procedures for subsequent management.
Technical Measures
The Kyocera Group has implemented the following technical measures to strengthen information security. These measures serve to strengthen information security and defend against cyberattacks.
- Cyber Hygiene Initiatives
The Kyocera Group monitors the security status of the entire system in real time, using tools to quickly detect and take effective countermeasures against vulnerabilities. As a result, cyber hygiene is thoroughly practiced. In environments open to the public, third-party* vulnerability assessments are conducted at least once each year to strengthen defense measures against external attacks and to ensure the safety of the system. - Strengthen Resilience
The Kyocera Group has platform, detection, and response systems in place to strengthen resilience against cyberattacks. This minimizes damage by making it possible to quickly detect and effectively respond to attacks. - Predictive Monitoring
The Kyocera Group uses services to monitor for signs of cyber incidents. As a result, we are able to detect potential threats at an early stage and take prompt action to prevent incidents from occurring.
A third-party organization that provides services compliant with the "Information Security Service Standards" established by the Ministry of Economy, Trade and Industry
Kyocera Joins the Nippon CSIRT Association
In January 2021, Kyocera officially joined the Nippon CSIRT Association. Through the activities of this council, we will strive to improve the security level of the entire Kyocera Group by sharing security incidents and vulnerability information with other member companies.
●Nippon CSIRT Association
・Official name of the team:KYOCERA Security Incident Response Team.
・Team abbreviation:KC-SIRT
・Organization name:KYOCERA Corporation
Public Announcement of Security Incidents
Security incidents at our company are publicly announced on our company website.
●March 10, 2023 Suspected information leakage due to unauthorized access to Fujitsu Limited FENICS Internet Service
●June 1, 2023 Regarding the Cybersecurity Incident at the U.S. Subsidiary
Efforts to Protect Personal Information
Personal Information Protection Management System
The Kyocera Group regards the personal information obtained from stakeholders through business activities as important private information and strives to protect it thoroughly as a primary social responsibility. Kyocera has set up rules to protect specific personal information, clarified personal information usage purposes, set up a dedicated contact for inquiries, and provides regular education to employees handling private information, thereby ensuring thorough management. Also, regulations for Personal Information Protection have been established for employees to establish basic matters regarding the safeguarding of personal information, including a code of conduct for employees who handle personal information and the use of personal information management ledgers to monitor the management status of personal information centrally. Kyocera strives to ensure correct handling of personal information to maintain society's trust by preventing personal information from being compromised. These Personal Information Protection Management Regulations require employees to take necessary measures such as contacting related divisions, preventing the spread of damage, and carrying out investigations if personal information is leaked. Cases such as the leakage of personal details are incorporated into Kyocera's risk management policy by establishing the Kyocera Group Information Security Regulations. The Personal Information Protection Management Regulations also stipulate that employees may be subject to disciplinary action if personal information is compromised. Kyocera strives to disseminate its Personal Information Protection Policy and Personal Information Protection Management Regulations within the company and enhance its effectiveness through regular training, surveys, and audits.

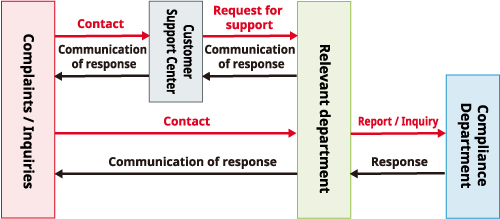
Communication System on Personal Information